Networks Nozomi Networks na próxima fase de crescimento com a conclusão da aquisição pela Mitsubishi Electric
Leia as notíciasGuardian Air is a wireless sensor that, when integrated with the Nozomi Vantage cloud platform, provides much-needed visibility into wirelessly enabled assets, their behavior and correlated risk.
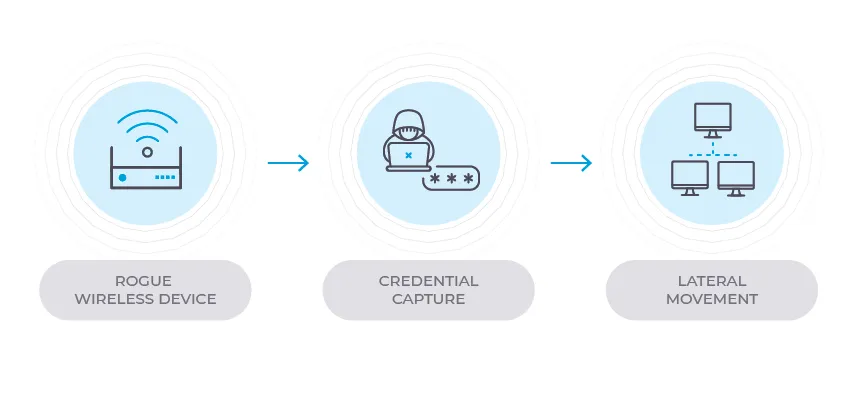
Wireless devices may never touch the network yet still communicate with critical assets, exfiltrate data and interfere with control signals, all undetected
Increasing reliance on wireless communications for logistics, autonomous transport and monitoring expands the attack surface
As both a broadcast and shared medium, wireless signals are susceptible to interception, eavesdropping and Man-in-the-Middle attacks
Appearing and disappearing from the RF spectrum makes it hard to baseline normal wireless asset behavior and detect anomalies
Bad actors just need proximity (from a rooftop, vehicle or drone) to bypass perimeter defenses, connect wirelessly and pull off an attack
Guardian Air continuously monitors wireless spectrum technologies operating between 800 MHz and 5895 MHz to reveal the prevalence and types of wireless devices in your environment, what protocols they use and their risks.
Detects a wide range of wireless-specific threats, providing security teams with the right data about the electromagnetic spectrum for faster response.
Sends data collected from wireless-enabled devices to the Nozomi Vantage platform for analysis and correlation with network and endpoint telemetry that enables you to detect complex threats with multiple vectors.